Community safety greatest practices units the stage for a complete understanding of the measures that may be taken to safeguard digital info and networks. A strong basis in community safety greatest practices is important in immediately’s more and more complicated digital panorama, the place information breaches and cyber assaults have gotten extra frequent and complex.
The Artikel supplied presents a broad vary of subjects associated to community safety greatest practices, from entry management and authentication to community system safety and vulnerability administration. Every part delves into the intricacies of community safety, offering readers with a radical understanding of the ideas and strategies crucial to guard networks from numerous varieties of threats.
Community Safety Fundamentals: Community Safety Finest Practices
Community safety is a vital facet of recent computing, safeguarding delicate info and stopping unauthorized entry to laptop techniques and networks. A complete strategy to community safety includes implementing numerous measures to guard towards malicious actions, together with unauthorized entry, information breaches, and different cyber threats. On this part, we are going to focus on the significance of entry management, community segmentation, widespread community safety threats and vulnerabilities, and the function of firewalls in community safety.
Entry Management
Entry management is a elementary facet of community safety, specializing in regulating consumer entry to community assets and information. Efficient entry management ensures that solely approved people have entry to delicate info and system assets. That is sometimes achieved by the usage of authentication mechanisms, akin to username/password mixtures, good playing cards, or biometric authentication.
Entry management is carried out utilizing a set of insurance policies and procedures that outline consumer roles, entry rights, and permissions. These insurance policies should be often reviewed and up to date to make sure they continue to be efficient and compliant with organizational safety insurance policies. Entry management measures might be categorized into three main varieties:
- The necessity-to-know precept: Customers are granted entry solely to info and assets essential to carry out their job features.
- The least privilege precept: Customers are granted the minimal set of privileges required to carry out their job features.
- Separation of duties: Totally different people or teams are chargeable for performing vital operations, guaranteeing that no single particular person can compromise safety.
Community Segmentation
Community segmentation includes dividing a community into smaller segments or sub-networks, every with its personal set of safety insurance policies and entry controls. This strategy improves community safety by lowering the assault floor and limiting the unfold of malware and different safety threats.
Community segmentation might be carried out utilizing numerous strategies, together with:
- Digital LANs (VLANs): Sub-networks are created utilizing VLANs, that are remoted from one another utilizing network-layer (Layer 3) switching.
- Digital Non-public Networks (VPNs): VPNs are used to create safe, encrypted connections between two or extra networks.
Widespread Community Safety Threats and Vulnerabilities
Community safety threats and vulnerabilities might be categorized into a number of varieties, together with:
- Malware: Software program designed to hurt or exploit a pc system, akin to viruses, worms, and trojans.
- Denial-of-service (DoS) and distributed denial-of-service (DDoS) assaults: Overwhelming a community or system with visitors or requests to render it inaccessible.
- Phishing: Makes an attempt to trick customers into revealing delicate info or performing malicious actions.
Position of Firewalls in Community Safety
Firewalls are community safety techniques that monitor and management incoming and outgoing community visitors primarily based on predetermined safety guidelines. They play a vital function in defending networks from unauthorized entry and malicious actions.
Firewalls might be categorized into two main varieties:
- Community firewalls: Examine community visitors and block malicious or unauthorized entry makes an attempt.
- Host-based firewalls: Put in on particular person computer systems, these firewalls examine and regulate visitors on a per-host foundation.
Firewalls might be configured to dam or permit incoming and outgoing visitors primarily based on a wide range of elements, together with:
- IP addresses and ports
- Protocols (e.g., HTTP, FTP)
- Supply and vacation spot IP addresses
Firewalls can be configured to implement community deal with translation (NAT), which permits a number of personal IP addresses to be mapped to a single public IP deal with, bettering community safety and lowering the assault floor.
Authentication and Authorization

Authentication and authorization are two distinct ideas in community safety that make sure the integrity and safety of knowledge and techniques. Authentication refers back to the technique of verifying the identification of a consumer or system, whereas authorization determines what actions a official consumer or system can carry out.
Forms of Authentication Strategies
There are three main varieties of authentication strategies utilized in community safety: passwords, biometrics, and good playing cards.
- Password-based authentication is essentially the most generally used methodology. A password is a secret string of characters recognized solely to the consumer that’s supplied to the system to achieve entry. Passwords ought to be a minimum of 12 characters lengthy, embrace a mixture of uppercase and lowercase letters, digits, and particular characters, and shouldn’t be simply guessable or just like any earlier passwords.
- Biometric authentication includes the usage of bodily or behavioral traits akin to fingerprints, facial recognition, or iris scans to determine a consumer. This methodology gives a excessive stage of safety and is tough to copy or bypass.
- Good card-based authentication includes the usage of a card with a built-in microprocessor that shops encryption keys and certificates. The cardboard is used to authenticate and authorize customers, and it gives a further layer of safety.
Position-Based mostly Entry Management (RBAC)
Position-Based mostly Entry Management (RBAC) is a safety strategy that assigns permissions to customers primarily based on their function inside a company. The concept behind RBAC is to assign a set of permissions to a selected function after which assign that function to a consumer. This makes it simpler to handle entry and permissions for giant numbers of customers.
Position-Based mostly Entry Management (RBAC) is outlined as “A safety strategy that assigns permissions to customers primarily based on their function inside a company.”
Implementing Multi-Issue Authentication
Implementing multi-factor authentication (MFA) includes utilizing multiple issue to confirm the identification of a consumer. This will embrace a mixture of one thing a consumer is aware of (akin to a password), one thing a consumer has (akin to a sensible card), and one thing the consumer is (akin to a fingerprint).
- One-Time Passwords (OTPs): An OTP is a password that’s legitimate for less than a brief interval, making it tough for attackers to make use of. OTPs might be despatched by way of SMS or generated by an authenticator app.
- Banking Tokens: A financial institution token is a small system that generates a novel password that modifications steadily, including an additional layer of safety.
- U2F: U2F stands for Common 2nd Issue, which makes use of a {hardware} token, akin to a USB system, to confirm a consumer’s identification.
- MFA Apps: MFA apps, akin to Google Authenticator or Authy, generate time-based OTPs that can be utilized to authenticate a consumer.
Usually Updating and Rotating Passwords
Usually updating and rotating passwords is important to take care of the safety of a system. This includes altering passwords often and utilizing a password supervisor to maintain monitor of a number of passwords.
- Passwords ought to be modified a minimum of each 60 to 90 days, and this ought to be finished mechanically by the system.
- Passwords ought to be complicated, together with a mixture of uppercase and lowercase letters, digits, and particular characters.
- Password managers can be utilized to generate and retailer complicated passwords, making it simpler to handle a number of passwords.
Community Safety Protocols
Community safety protocols play an important function in guaranteeing the confidentiality, integrity, and availability of community communications. These protocols present a safe approach to transmit information over the web and shield towards unauthorized entry, eavesdropping, and information tampering.
Distinction between IPv4 and IPv6
IPv4 (Web Protocol model 4) and IPv6 (Web Protocol model 6) are two variations of the web protocol used for routing visitors on the web. IPv4 makes use of 32-bit addresses, whereas IPv6 makes use of 128-bit addresses. This main distinction permits IPv6 to offer a just about limitless variety of IP addresses, making it a vital improve for the ever-growing web.
IPv4 addresses are represented in a dotted decimal format, akin to 192.0.2.1, whereas IPv6 addresses are represented in a hexadecimal format, akin to 2001:0db8:85a3:0000:0000:8a2e:0370:7334. This enhance in deal with area permits IPv6 to deal with the rising variety of units and supply extra options, akin to improved safety and high quality of service.
Significance of Safe Sockets Layer/Transport Layer Safety (SSL/TLS)
SSL/TLS (Safe Sockets Layer/Transport Layer Safety) is a cryptographic protocol that gives safe communication between an internet server and a consumer, akin to an internet browser. It ensures the confidentiality, integrity, and authenticity of knowledge exchanged between the server and the consumer, defending towards eavesdropping, tampering, and man-in-the-middle assaults.
SSL/TLS works by encrypting information utilizing a symmetric key, which is shared between the server and the consumer. This encrypted information is then transmitted over the web, guaranteeing that solely the meant events can decrypt and entry it. SSL/TLS is broadly utilized in e-commerce, on-line banking, and different safe on-line transactions.
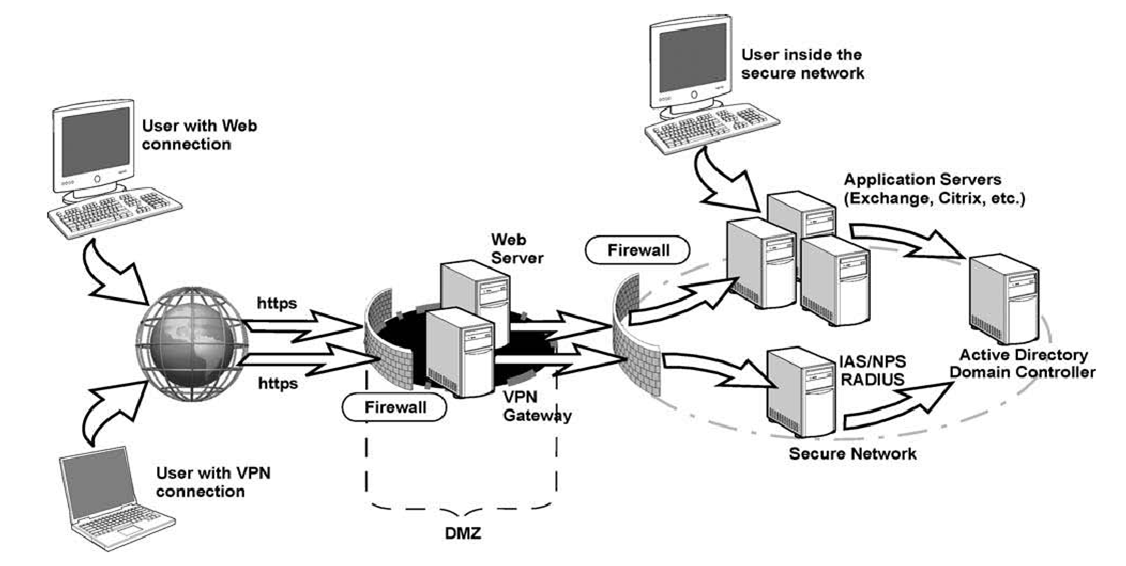
Implementing Digital Non-public Networks (VPNs)
A Digital Non-public Community (VPN) is a safe community connection between two or extra units over the web. It gives a personal and safe tunnel for information transmission, encrypting information and defending towards unauthorized entry.
To implement a VPN, the next steps are adopted:
- Set up and configure VPN software program or {hardware} on the system.
- Set up a safe connection to the VPN server.
- Authenticate the consumer with a username and password or different authentication methodology.
- Encrypt information and transmit it over the VPN tunnel.
Position of Web Protocol Safety (IPSec) in community safety
IPSec (Web Protocol Safety) is a set of protocols that gives safety for IP communications by encrypting and authenticating information. It gives a safe methodology for transmitting IP packets between units, defending towards unauthorized entry and information tampering.
IPSec consists of two protocols: Authentication Header (AH) and Encapsulating Safety Payload (ESP). AH gives authentication and integrity, guaranteeing that information will not be tampered with, whereas ESP gives confidentiality by encrypting information.
Configuring community safety protocols on widespread community units
Community units, akin to routers and switches, might be configured to implement community safety protocols, akin to ACLs, firewall guidelines, and VPN configurations.
To configure community units, comply with these steps:
- Login to the system’s internet interface or command-line interface.
- Navigate to the safety or firewall configuration web page.
- Configure ACLs or firewall guidelines to permit or deny particular visitors.
- Configure VPN settings, akin to server IP deal with and authentication methodology.
Wi-fi Community Safety
Wi-fi community safety is a vital part of community safety, as wi-fi networks are more and more getting used to attach units and supply entry to community assets. Wi-fi networks supply the comfort of mobility, however in addition they introduce new safety dangers. On this part, we are going to focus on the fundamentals of wi-fi networking, the significance of WPA2 (or WPA3) encryption, configuring wi-fi community entry management, the function of wi-fi intrusion detection techniques (WIDS), and securing wi-fi community entry factors (APs).
Primary Ideas of Wi-fi Networking
Wi-fi networking makes use of radio waves to transmit information between units. The most typical wi-fi networking know-how is Wi-Fi, which makes use of the two.4 GHz and 5 GHz frequency bands. Wi-Fi units use a way referred to as spread-spectrum to transmit information over the airwaves.
Significance of WPA2 (or WPA3) Encryption for Wi-fi Networks
WPA2 (or WPA3) encryption is a vital part of wi-fi community safety. WPA2 makes use of a symmetric key algorithm to encrypt information, whereas WPA3 makes use of a brand new algorithm referred to as ChaCha20-Poly1305. WPA2 encryption ensures that information transmitted over the airwaves is safe and can’t be intercepted by unauthorized units. WPA3 encryption gives even stronger safety and is a advisable improve for wi-fi networks.
- WPA2 and WPA3 encryption present a minimal of 128-bit encryption power, offering sturdy safety towards unauthorized entry.
- WPA2 and WPA3 encryption use a way referred to as TKIP (Temporal Key Integrity Protocol) to forestall replay assaults and guarantee safe key alternate.
Blockquote: “A safe wi-fi community is one which makes use of sturdy encryption, safe password insurance policies, and up-to-date encryption protocols.” (Supply: IEEE 802.11i normal)
Configuring Wi-fi Community Entry Management
Wi-fi community entry management refers back to the technique of controlling who can entry a wi-fi community and what assets they will entry. Configuring wi-fi community entry management includes establishing a RADIUS (Distant Authentication Dial-In Person Service) server to authenticate customers earlier than granting them entry to the community. The RADIUS server can use a wide range of authentication strategies, akin to username and password, good playing cards, or biometric scanners.
Position of Wi-fi Intrusion Detection Methods (WIDS)
Wi-fi intrusion detection techniques (WIDS) are software program or {hardware} home equipment designed to detect and stop wi-fi assaults. WIDS techniques monitor the airwaves for suspicious exercise, akin to unauthorized entry makes an attempt or malware transmission.
Securing Wi-fi Community Entry Factors (APs)
Securing wi-fi community entry factors (APs) requires a mixture of bodily and logical safety measures. Bodily safety measures embrace bodily securing the AP to forestall tampering or theft. Logical safety measures embrace configuring the AP to make use of WPA2 (or WPA3) encryption, establishing a RADIUS server, and configuring the AP for visitor entry.
| Advantages of Securing Wi-fi Community Entry Factors (APs) | ||
|---|---|---|
| Prevents unauthorized entry makes an attempt | Helps to forestall malware transmission | Protects delicate information |
Finest Practices for Securing Wi-fi Networks
To safe wi-fi networks, comply with these greatest practices:
- Use WPA2 (or WPA3) encryption for all wi-fi networks
- Configure wi-fi community entry management to require customers to authenticate earlier than getting access to the community
- Usually replace software program and firmware for all wi-fi community units
- Implement a WIDS system to detect and stop wi-fi assaults
Knowledge Backup and Restoration
Knowledge backup and restoration are essential elements of a complete community safety technique. Dropping necessary information might be devastating for organizations, making it important to implement common information backups and have a dependable information restoration plan in place.
Efficient information backup and restoration processes be sure that enterprise continuity is maintained, even within the occasion of a catastrophe. On this part, we’ll discover the significance of standard information backups, focus on numerous information restoration strategies, and study widespread information backup and restoration instruments.
Significance of Common Knowledge Backups
Common information backups are important for shielding towards information loss as a consequence of numerous causes akin to {hardware} failure, software program corruption, human error, or pure disasters. With common backups, you may be sure that your information is secure and might be restored shortly within the occasion of a catastrophe.
- Knowledge backups present a security web towards information loss, permitting you to revive your information shortly and reduce downtime.
- Common backups be sure that your information is up-to-date, lowering the danger of knowledge inconsistencies and errors.
- Knowledge backups present a backup of your information, permitting you to check and validate your backups often.
Knowledge Restoration Strategies
Knowledge restoration strategies contain strategies used to get better information from backups or secondary storage units. Snapshotting and replication are two widespread information restoration strategies utilized in community safety.
Snapshotting includes creating a replica of knowledge at a selected time limit, permitting for fast restoration within the occasion of a catastrophe.
- Snapshots present a point-in-time copy of knowledge, making it simpler to get better information from a selected time limit.
- Snapshots scale back the danger of knowledge corruption and inconsistencies, guaranteeing that your information is constant and dependable.
Knowledge Backup and Restoration Instruments
Numerous information backup and restoration instruments can be found, together with software program and {hardware} options. These instruments assist streamline the info backup and restoration course of, making it simpler to guard and get better information.
- Software program options, akin to backup software program, can automate information backups and recoveries, lowering the danger of human error.
- Cloud-based backup options permit for distant information backups and recoveries, making it simpler to handle information throughout a number of places.
Position of Knowledge Backup and Restoration in Catastrophe Restoration Planning
Knowledge backup and restoration play a vital function in catastrophe restoration planning, guaranteeing enterprise continuity within the occasion of a catastrophe.
- Knowledge backups present a method of recovering information shortly, minimizing downtime and lowering the danger of knowledge loss.
- Knowledge restoration plans be sure that enterprise operations can proceed even within the occasion of a catastrophe.
Securing Knowledge Backups and Restoration Processes
Securing information backups and restoration processes is important to forestall information breaches and unauthorized entry.
- Use safe protocols, akin to encryption, to guard information backups and recoveries.
- Implement entry controls and authorization mechanisms to make sure that solely approved personnel can entry information backups and recoveries.
Vulnerability Administration
Vulnerability administration is a vital facet of community safety that includes figuring out, prioritizing, and addressing vulnerabilities in a company’s techniques, purposes, and infrastructure. Efficient vulnerability administration requires a proactive strategy to scale back the danger of safety breaches and information theft.
The Position of Vulnerability Evaluation Instruments in Community Safety
Vulnerability evaluation instruments play a vital function in vulnerability administration by serving to organizations determine and prioritize vulnerabilities of their techniques and purposes. These instruments use numerous strategies, akin to community scanning, vulnerability scanning, and configuration evaluation, to determine potential vulnerabilities and supply suggestions for remediation.
Standard vulnerability evaluation instruments embrace Nessus, OpenVAS, and Qualys.
Vulnerability evaluation instruments might help organizations determine vulnerabilities earlier than they’re exploited by attackers, lowering the danger of safety breaches and information theft.
The Significance of Usually Scanning for Vulnerabilities
Common vulnerability scanning is important to make sure that a company’s techniques and purposes are safe and free from vulnerabilities. Vulnerability scanning ought to be carried out regularly, ideally weekly or month-to-month, to determine new vulnerabilities and assess the effectiveness of present remediation efforts.
- Vulnerability scans assist determine new vulnerabilities which will have been launched by updates, patches, or new software program installations.
- Vulnerability scans assess the effectiveness of present remediation efforts and supply suggestions for additional enchancment.
- Vulnerability scans assist determine vulnerabilities which will have been missed or missed throughout earlier scans.
Figuring out and Prioritizing Vulnerabilities, Community safety greatest practices
Figuring out and prioritizing vulnerabilities is a vital step in vulnerability administration. Vulnerabilities ought to be prioritized primarily based on their severity, exploitability, and potential affect on the group.
- Vulnerabilities ought to be prioritized primarily based on their Widespread Vulnerability Scoring System (CVSS) rating, which assesses the severity and exploitability of the vulnerability.
- Vulnerabilities ought to be prioritized primarily based on their potential affect on the group, together with the potential for information theft, disruption of enterprise operations, or reputational harm.
- Vulnerabilities ought to be prioritized primarily based on the chance of exploitation by attackers.
Examples of Widespread Vulnerability Administration Instruments
A number of in style vulnerability administration instruments can be found, together with:
- Nessus: A complete vulnerability scanning device that gives detailed info on vulnerabilities and suggestions for remediation.
- OpenVAS: An open-source vulnerability scanning device that gives a complete vulnerability administration platform.
- Qualys: A cloud-based vulnerability administration platform that gives vulnerability scanning, remediation suggestions, and steady monitoring.
The Position of Vulnerability Administration in Incident Response Planning
Vulnerability administration performs a vital function in incident response planning by serving to organizations determine and mitigate vulnerabilities that could be exploited by attackers.
- Vulnerability administration helps determine vulnerabilities that could be exploited by attackers, permitting organizations to take proactive measures to mitigate the danger.
- Vulnerability administration helps assess the potential affect of a safety breach, together with the potential for information theft, disruption of enterprise operations, or reputational harm.
- Vulnerability administration helps determine alternatives for steady enchancment in safety controls and procedures.
Compliance and Governance
Compliance and governance are vital elements of a strong community safety technique. Efficient compliance and governance assist organizations be sure that they’re assembly regulatory necessities, minimizing the danger of safety breaches, and sustaining confidentiality, integrity, and availability (CIA) of delicate information.
### Significance of Compliance with Regulatory Necessities
Regulatory necessities akin to HIPAA (Well being Insurance coverage Portability and Accountability Act) and PCI-DSS (Cost Card Business Knowledge Safety Normal) are in place to guard delicate information and stop safety breaches. Compliance with these laws is important for organizations dealing with delicate information. Failure to conform may end up in vital fines and reputational harm.
Compliance necessities might embrace:
Make sure the confidentiality, integrity, and availability of delicate information as per regulatory necessities.
### Position of Governance Frameworks in Community Safety
Governance frameworks akin to COBIT (Management Aims for Data and Associated Know-how) and ITIL (Data Know-how Infrastructure Library) present a construction for organizations to handle and govern their IT assets successfully. These frameworks assist organizations align their IT technique with enterprise targets, guaranteeing that community safety is an integral a part of the general governance framework.
Key areas ruled by COBIT and ITIL embrace:
*
Danger Administration
Danger administration is a vital part of community safety governance. It includes figuring out, assessing, and mitigating potential dangers to the group’s IT assets. Danger administration helps organizations prioritize their safety efforts and be sure that they’re investing in risk-reducing measures successfully.
Service Administration
Service administration is one other key space ruled by COBIT and ITIL. It includes managing IT companies to fulfill the wants of the enterprise, guaranteeing that they’re safe, accessible, and dependable. Service administration helps organizations be sure that their community safety is aligned with enterprise targets and that safety measures are built-in into service supply.
Data Safety Administration
Data safety administration is a vital part of community safety governance. It includes managing info safety to guard delicate information and stop safety breaches. Data safety administration helps organizations be sure that their community safety is aligned with regulatory necessities and that safety measures are efficient in stopping safety breaches.
### Implementing Compliance and Governance Finest Practices in Community Safety
To implement compliance and governance greatest practices in community safety, organizations ought to:
-
Set up a transparent community safety coverage that Artikels the group’s safety targets, roles, and obligations.
-
Implement a danger administration framework that identifies, assesses, and mitigates potential dangers to the group’s IT assets.
-
Develop an incident response plan that Artikels procedures for responding to safety incidents.
-
Conduct common safety audits to make sure compliance with regulatory necessities and determine areas for enchancment.
-
Preserve correct data of security-related incidents and compliance actions.
### Significance of Steady Monitoring and Reporting in Community Safety
Steady monitoring and reporting are important elements of a strong community safety technique. They assist organizations determine safety incidents early, reply shortly, and preserve compliance with regulatory necessities.
Key advantages of steady monitoring and reporting embrace:
*
Early Detection of Safety Incidents
Steady monitoring helps organizations detect safety incidents early, lowering the danger of knowledge breaches and reputational harm.
Improved Incident Response
Steady monitoring permits organizations to reply shortly to safety incidents, lowering the scope of harm and minimizing downtime.
Compliance with Regulatory Necessities
Steady monitoring helps organizations preserve compliance with regulatory necessities, lowering the danger of fines and reputational harm.
### Addressing Compliance and Governance in Community Safety Audits
Community safety audits assist organizations determine areas of non-compliance with regulatory necessities and assess the effectiveness of their safety measures. Key areas audited embrace:
-
Compliance with regulatory necessities akin to HIPAA, PCI-DSS, and GDPR.
-
Effectiveness of danger administration and incident response procedures.
-
Safety measures in place to guard delicate information and stop safety breaches.
-
Compliance with governance frameworks akin to COBIT and ITIL.
-
Effectiveness of steady monitoring and reporting procedures.
Abstract
In conclusion, community safety greatest practices are a vital part of sustaining a safe on-line presence. By understanding the significance of entry management, authentication, and community segmentation, amongst different measures, organizations can considerably scale back their vulnerability to cyber assaults and information breaches. Moreover, adopting greatest practices in community system safety, information backup and restoration, and vulnerability administration might help organizations get better shortly and effectively within the occasion of an incident.
FAQ Abstract
Q: What’s the main perform of entry management in community safety?
A: The first perform of entry management in community safety is to control and prohibit consumer entry to delicate areas of the community, primarily based on their identities or roles.
Q: How can multi-factor authentication improve community safety?
A: Multi-factor authentication can improve community safety by requiring customers to offer a number of types of verification, akin to a password and a biometric scan, making it harder for unauthorized customers to achieve entry to the community.
Q: What’s the significance of often updating and rotating passwords in community safety?
A: Usually updating and rotating passwords in community safety is important in stopping password-based assaults, akin to cracking and phishing, and guaranteeing that passwords usually are not shared or compromised.
Q: How can firewalls be used to boost community safety?
A: Firewalls can be utilized to dam or filter incoming and outgoing community visitors, primarily based on predetermined safety guidelines, to forestall unauthorized entry, malware, and different varieties of community threats.
Q: What’s the function of VPNs in community safety?
A: VPNs play a vital function in community safety by making a safe and encrypted connection between the consumer’s system and the community, permitting customers to entry delicate information from distant places with out compromising the community.