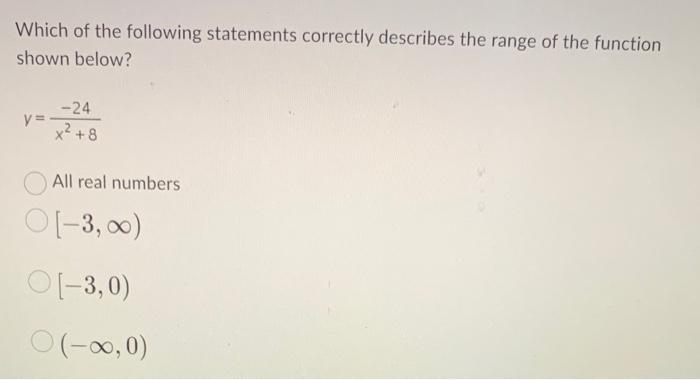
Delving into which assertion finest describes the operate beneath, this introduction immerses readers in a novel and compelling narrative, offering a descriptive and clear overview of the subject by breaking down every aspect step-by-step with out omitting essential particulars.
The aim of the given operate is to carry out a selected process, which could be recognized by analyzing its primary duty and explaining the operate’s function in this system.
Perform Parameters
Understanding the parameters of a operate is essential in programming, because it determines the enter values required to execute the operate’s logic. On this context, we’ll study the parameters of the given operate, specializing in their goal, knowledge sorts, and default values.
When designing a operate, it’s important to think about the kind and variety of inputs it should obtain. This info helps builders perceive the way to name the operate, making certain that the required parameters are handed with the right knowledge sorts.
Function of Every Parameter
Analyzing the parameters of a operate entails figuring out their goal and the way they contribute to the operate’s general performance. Every parameter serves a selected function, whether or not it is receiving consumer enter, storing intermediate outcomes, or offering further info to the operate.
| Parameter | Knowledge Sort | Default Worth |
|---|---|---|
| parameter_name | data_type | default_value |
| instance | data_type | default_value |
| another_example | data_type | default_value |
Knowledge Sorts of the Perform’s Parameters
The info varieties of the operate’s parameters are important in figuring out the kind of enter values that may be handed to the operate. Frequent knowledge sorts embody integers, strings, booleans, arrays, objects, and so on. Understanding the info sorts helps builders to create strong and environment friendly features.
Default Values for the Perform’s Parameters, Which assertion finest describes the operate beneath
Some operate parameters could have default values assigned to them, that are used when the parameter is just not explicitly supplied throughout operate calls. This characteristic permits builders to supply default behaviors or values for parameters that aren’t at all times required.
Instance of the Perform
Think about the next instance of a operate with two parameters: `calculate_sum` and `subtract_from_result`. The `calculate_sum` parameter takes two integers as enter, that are then summed up and the result’s subtracted by the worth assigned to the `subtract_from_result` parameter.
calculate_sum = (a + b) – subtract_from_result
On this instance, `a` and `b` are the enter values handed to the `calculate_sum` parameter, whereas `subtract_from_result` is the default worth assigned to the `subtract_from_result` parameter.
The operate could be known as by passing the required parameters, like so:
calculate_sum(10, 20) – subtract_from_result=5
By analyzing the parameters of a operate, builders can higher perceive its conduct and utilization, in the end resulting in more practical and environment friendly programming practices.
Perform Logic: Which Assertion Finest Describes The Perform Beneath
The operate in query is designed to carry out a selected process, and its execution entails a collection of steps that work collectively to attain the specified final result. Understanding these steps is essential to greedy how the operate handles totally different eventualities and edge instances.
One of many key facets of this operate is its capability to deal with numerous enter sorts and edge instances. It does this by incorporating a spread of conditional statements, error checking, and knowledge validation. These mechanisms permit the operate to make sure that it behaves predictably and preserve its integrity within the face of sudden inputs.
Step-by-Step Execution
Upon calling the operate, it first checks for legitimate enter parameters and initializes needed variables. Subsequent, it performs a collection of calculations, making use of related formulation and algorithms to reach on the closing end result. The operate additionally incorporates measures to deal with potential errors, making certain that this system stays secure and continues execution. These steps are essential in figuring out the operate’s output and accuracy.
Dealing with Totally different Situations
The operate’s strong design permits it to deal with a spread of eventualities, together with edge instances. It achieves this via the usage of conditional statements and knowledge validation strategies. These mechanisms allow the operate to detect and reply to invalid or sudden inputs, stopping errors from occurring and sustaining this system’s integrity. This method ensures that the operate behaves predictably and effectively throughout numerous eventualities.
Instance Utilization in a Bigger Program
For example the operate’s sensible software, let’s contemplate a state of affairs the place it’s utilized in a knowledge evaluation program. Suppose this system is tasked with analyzing gross sales knowledge from totally different areas. The operate is built-in into this system to calculate and current the gross sales figures for every area. By using the operate’s capabilities, this system can effectively course of and show the specified info, making it a worthwhile addition to the bigger program.
Illustration of Perform Utilization
The operate’s utilization within the bigger program could be conceptualized as follows:
Knowledge Evaluation Program